You have probably already heard of Microsoft Copilot and wondered how exactly this tool works and whether your data entered into it is secure. In this guide, I will provide you with all the important information about the functionality of Microsoft Copilot and address the security aspects that should be of interest to you as a user. After reading this, you will understand how to efficiently utilize Copilot and whether you need to be concerned about the security of your information.
Key Takeaways
- Your queries to Microsoft Copilot are secure and not used for training OpenAI models.
- The tool operates through various steps, starting with your inputted prompt, proceeding with grounding, and then making API requests to the OpenAI model.
- Microsoft ensures that your data, including emails, documents, and more, is not viewed or processed by third parties.
Step-by-Step Guide
In the following sections, I will explain the individual steps of how Microsoft Copilot works.
First, we start with the prompt, the text command you enter into the application. Your first step is to formulate a precise and clear prompt. This is crucial as the quality of your request directly affects the response you receive. For example, you can ask questions or request assistance, depending on what you need.
Once you have entered your prompt, it is forwarded to the Copilot system. Here, it is determined whether additional tools are required. This occurs in a process known as grounding. This means that the system analyzes the information needed to comprehensively answer your query. In this step, the tool decides whether internet access or other plugins are needed.
If your prompt requires additional support, these tools are activated. If not, this step is skipped. For example, if you ask for a story about the events of a specific day, it might be useful to utilize current internet data. For general questions like the start date of World War II, internet access is not needed.
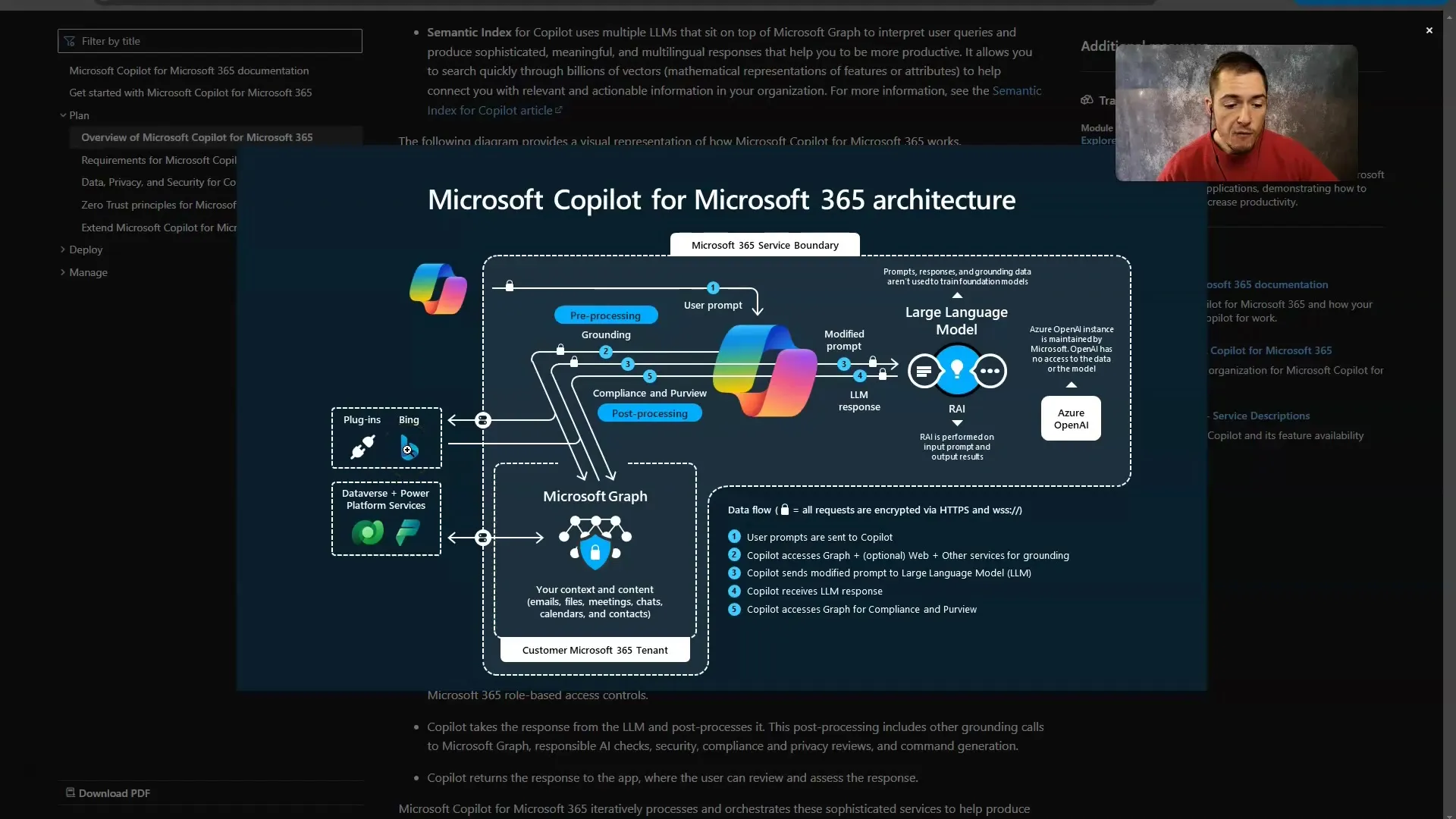
Once the necessary tools are identified, your request is sent to the OpenAI API, most likely using the GPT-4 Turbo model. The Copilot now sends the request for processing to the Large Language Model. It now analyzes your questions and provides a response.
It's important to know that Microsoft and OpenAI ensure that your information is not used to train their models during this processing. This means that your prompt, the searched data, and any other inputs are treated anonymously.
After the model processing, you will receive your output regardless of which Microsoft service you are using – whether it be in emails, files, meetings, or your calendar. Your output will be displayed in an understandable format. This ensures that interacting with Copilot is not only secure but also efficient.
In summary, the steps of the Copilot system can be described as follows: You input a prompt, which may be supplemented with tools such as internet access, before the request is forwarded to the Large Language Model. Subsequently, you receive your response – all while considering your data security.
Summary
In this guide, you have learned how Microsoft Copilot works and that your data is secure during use. From entering your prompts, through system analysis, to the return of responses – all steps are carried out with data security in mind. Multiple protective mechanisms and transparency from Microsoft and OpenAI are in place to safeguard your information.
Frequently Asked Questions
How is my prompt treated?Your prompt is anonymously processed and not used for training data.
Could someone access my inputs?No, Microsoft and OpenAI guarantee that your inputs are not viewed or used.
Do I need special knowledge to write good prompts?It helps to formulate precise and understandable questions, but specific knowledge is not required.
Is Microsoft Copilot safe to use?Yes, Microsoft promises that your data is protected and not used for training purposes.
How can I learn more about security?You can visit Microsoft's documentation for detailed information on data security.


